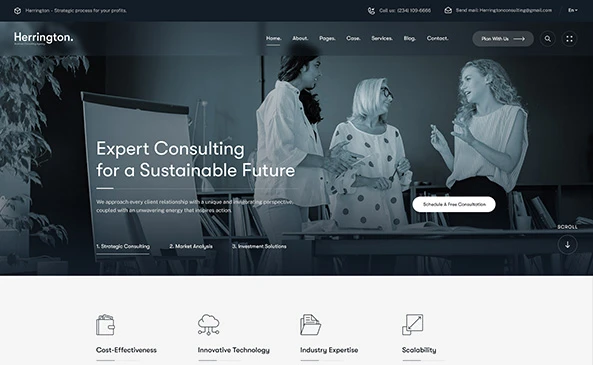
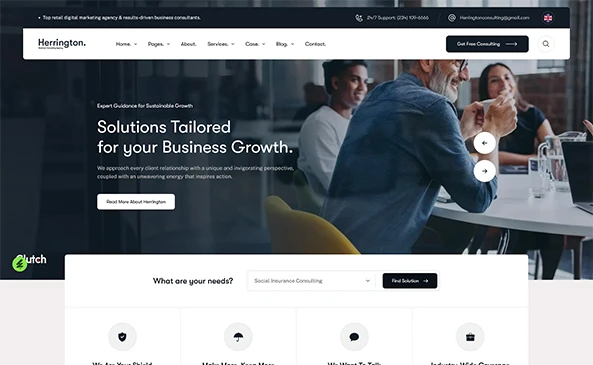
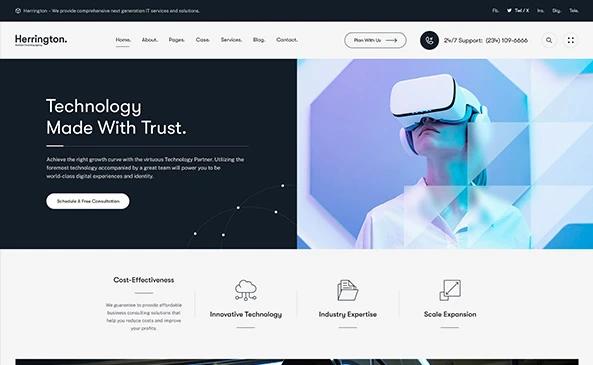
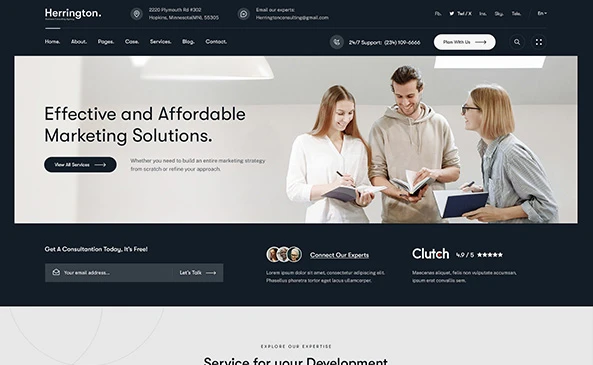
Our Process
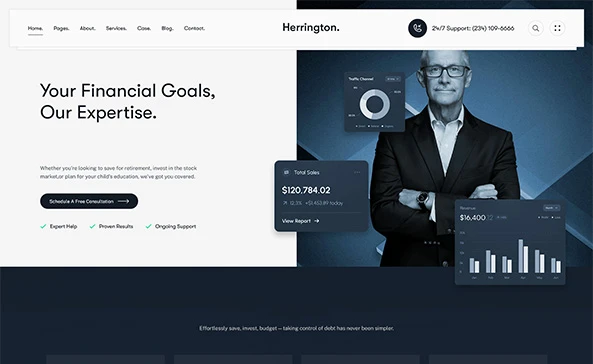
We Don’t Just Deliver Projects. We Deploy Control Systems.
Every operation is a structured engagement engineered for outcomes.
- Home Main
- Our Process
1

Step 1. Strategic Alignment
Diagnose opportunities, threats, and systemic bottlenecks.
We begin by analyzing your infrastructure, motivations, and mission-critical needs.
- A senior consultant meets with your core team to define goals and operational context
- A full Technical & Strategic Audit follows — including systems inventory, architecture mapping, and risk assessments
- Budget, timelines, and data security thresholds are scoped early to prevent delays
2

Step 2. System Architecture & Concept Mapping
Build the operating blueprint.
We convert your needs into actionable system designs.
- Project managers create a 2-week strategic roadmap defining SoW (Scope of Work) with tactical precision
- You’re onboarded into a secure, real-time collaboration space (Slack + Asana/Notion)
- All concepts are validated with technical feasibility checks, not hypotheticals
3

Step 3. Prototype, Test, and Pressure-Test
Validate before deployment.
We run operational simulations and validate assumptions through test sprints.
- Expect weekly iteration reviews with direct feedback loops
- If priorities shift, our teams re-architect in real time — no bureaucratic lag
- Task time is transparently tracked via Toggl, and clients receive daily email summaries
4

Step 4. Full-Scale Execution & Delivery
Operationalize, institutionalize, and future-proof the solution.
With stakeholder validation and system acceptance confirmed, we transition into full-scale execution. This isn’t just a deployment — it’s a deliberate, production-hardened rollout designed for resilience, sustainability, and seamless scalability across your enterprise infrastructure.
All components are stress-tested and configured for real-world performance. Systems are optimized for uptime, fortified for security, and fully documented for internal alignment and compliance. We don't just flip the switch — we embed operational excellence.
With stakeholder validation and system acceptance confirmed, we transition into full-scale execution. This isn’t just a deployment — it’s a deliberate, production-hardened rollout designed for resilience, sustainability, and seamless scalability across your enterprise infrastructure.
All components are stress-tested and configured for real-world performance. Systems are optimized for uptime, fortified for security, and fully documented for internal alignment and compliance. We don't just flip the switch — we embed operational excellence.
- All systems are production-hardened, documented, and optimized
- Handover includes SOPs, config repositories, security logs, and knowledge bases
- Post-deployment audits are included — so you're not left in the dark
Let’s Engineer It Together
This is Your Access Point.
From stealth-mode startups to government infrastructure. We don’t “do” projects — we deploy control frameworks that scale.